What is a Passkey? Is it different than a Password?
Are you using weak or out-of-date passwords? For many places in a business, passwords are the most often used method of authentication, but they can be among the weakest. They can be easy to guess, or steal. Many people use the same password across several accounts. All of these (very human!) habits can make you vulnerable to cyber attacks.
The sheer volume of passwords that we need to remember in this day and age is huge. Of course we develop habits to remember those passwords. Unfortunately those habits often make it easier for criminals to breach those accounts.
61% of all data breaches involve stolen or hacked login credentials.
In recent years, a better solution has emerged: passkeys. Passkeys are more secure than passwords, and are often more convenient as well.
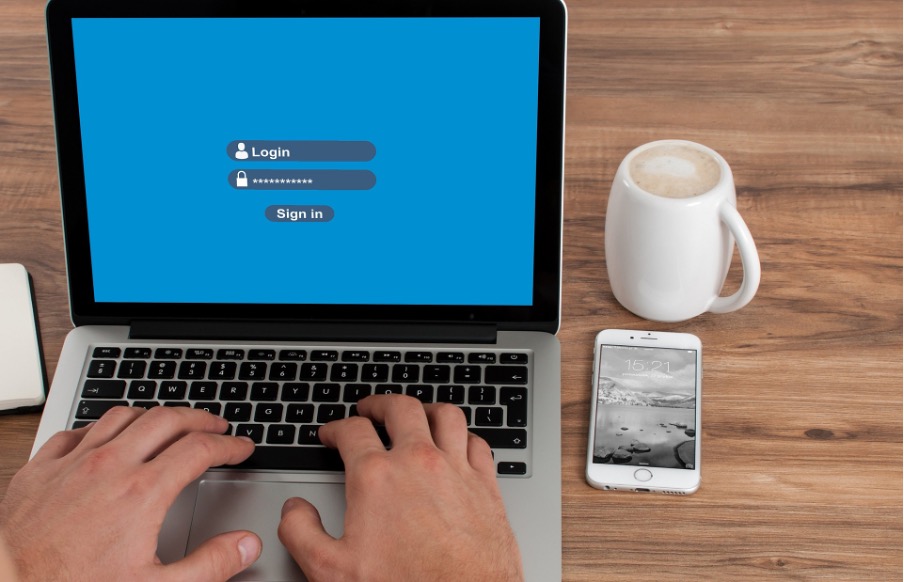
Are you using weak or out-of-date passwords? For many places in a business, passwords are the most often used method of authentication, but they can be among the weakest. They can be easy to guess, or steal. Many people use the same password across several accounts. All of these (very human!) habits can make you vulnerable to cyber attacks.
The sheer volume of passwords that we need to remember in this day and age is huge. Of course we develop habits to remember those passwords. Unfortunately those habits often make it easier for criminals to breach those accounts.
61% of all data breaches involve stolen or hacked login credentials.
In recent years, a better solution has emerged: passkeys. Passkeys are more secure than passwords, and are often more convenient as well.
What Is A Passkey?
The short answer is that pas
You can think of passkeys as a digital credential. A passkey allows someone to authenticate in a web service or cloud-based environment. Where passkeys are set up, you don’t need a username or password.
To get into the weeks a litt,e this authentication leverages Web Authentication (WebAuthn). This is a core component of FIDO2, an authentication protocol. Instead of using a unique password, it uses public-key cryptography for user verification. You as the user have an authentication key stored on your device. This could be a computer, mobile device, phone, or specific security-key device. The authentication key on your device is then used by the site to log the user in.
Passkeys work by generating a unique code for each login attempt. That code is validated by a server. The code is created by using a combination of information about the user and the decide that they are using the log in.
Why Should I Use A Passkey?
More Secure
Passkeys are more secure than passwords because they are more difficult to hack. Since the passkey uses your end device instead of something you remember, they are generated in a way that is harder to guess or fake. This is especially true in situations where biometric data is combined with your device data (e.g. using facial-recognition technology or fingerprints). The device data might be things like your location or devices MAC address. Combining those pieces of data means hackers are much less likely to be able to gain access to your accounts.
More Convenient
With password authentication, users need to remember more and more complex passwords. We’ve all seen the memes about how passwords nowadays require numbers, symbols, letters, a haiku, a gang sign and a magic spell. Remembering all of them (or forgetting them!) can slow you and your employees down. And resetting them can take up to 4 minutes on average.
Passkeys bypass this problem entirely by providing a single code. You can use that same code across all your accounts, making it much easier to log in and reducing the likelihood of forgetting or misplacing your password (and saving you time!).
Resistant to Phishing Attempts
Phishing scams are everywhere. Scammers might send an incredibly authentic-looking email with disguised links, fooling people to click and give the scammer their login information.
When you and your employees use passkeys instead, this method doesn’t work. Even if a hacker has your password, they don’t have the device passkey authentication to breach the account.
Is There Any Reason I Shouldn’t Use Passkeys?
Passkeys look like the future of authentication technology. But there can be some issues that you may run into when adopting them right now.
Passkeys Aren’t Yet Widely Used Yet
One of passkeys biggest drawbacks is the lack of adoption right now. Many websites and cloud services still rely on passwords. They don’t have passkey capability yet. Which leaves you as the business owner managing passwords for some accounts and passkeys for others. Untill passkeys become more widely adopted, this can mean awkward transitions.
Passkeys Need Extra Hardware & Software
Passwords are free and easy to use – every website these days has some password-gated information. They are everywhere, and you can make up a new one for each site you visit.
Passkeys need extra hardware and software to generate and validate the codes. This can be costly for businesses to put in place at first. But there is potential savings from improved security and user experience. I expect we will see the benefits continue to outweigh the drawbacks as this technology becomes more widely adopted.
Are Passkeys The Future of Security?
Passkeys are a more secure and convenient alternative to passwords. They are more difficult to hack, and they provide a more convenient way of logging into your accounts. But passkeys are not yet widely adopted. Additionally, businesses may need to budget for implementation.
Despite these challenges, passkeys represent a promising solution. Specifically, to the problem of weak passwords. They have the potential to improve cybersecurity. As well as boost productivity for businesses and individuals alike.
Need Help Improving Your Identity & Account Security?
Passkeys are just one of many options available to businesses right now to increase security. The investment might not be right for your business today, but at Hop-A-Long IT, security is always top of mind for your businesses.
Did you know that we offer a free security audit to go over the strength and weakness of your technical security? Call Hop-A-Long IT today at (785) 877-7001! We will go over how your business can stay strong, secure, and stress-free.
Article adapted with permission from The Technology Press
Looking for more to read?
You deserve stress-free IT.
Give us a call at (785) 877-7001. We can’t wait to make your life easier!
